What's new with SELinux in Fedora 19
Daniel J Walsh
Senior Principal Software Engineer
@rhatdan, danwalsh.livejournal.com, dwalsh@redhat.com
Saturday Aug 10 2013
Domains?
735 total domain
71 unconfined domains
disable unconfine.pp module (semodule -d unconfined)
11 unconfined domains
New Confined Domains F19
| pkcsslotd_t | manages PKCS#11 objects |
| slpd_t | Server Location Protocol Daemon |
| sensord_t | Sensor information logging daemon |
| mandb_t | Cron job used to create /var/cache/man content |
| glusterd_t | policy for glusterd service |
| stapserver_t | Instrumentation System Server |
| realmd_t | manages discovery/enrollment in AD/IPA realms/domains |
| phpfpm_t | FastCGI Process Manager |
New Permissive Domains F19
| systemd_localed_t | systemd service to change the system locale settings. |
| systemd_hostnamed_t | systemd service used change the system hostname. |
| systemd_sysctl_t | systemd early-boot service configures sysctl(8) parameters. |
| httpd_mythtv_script_t | mythtv cgi scripts manage mythtv scheduling and content. |
| openshift_cron_t | Cron jobs for openshift |
| swift_t | OpenStack Object Storage Server |
sepolicy tool chain
booleans - Description of booleans
communicate - Can domains communicate with each other
generate - Generate SELinux Policy module template
gui - New Application Centry Graphical User Interface
interface - See SELinux Policy interfaces
manpage - Generate SELinux man pages
network - See network information
transition - See how domain can transition to the target domain
sepolicy Demonstration
SELinux and Containers
http://people.fedoraproject.org/~dwalsh/SELinux/Presentations/openshift_selinux.ogvIf a file object is mislabeled you will get errors?

Someone put Skittles in the M&M dispenser!!!

Classic SELinux issue
vi ~/index.html
sudo mv ~/index.html /var/www/html
# wget localhost --2013-08-08 11:33:24-- http://localhost/ Resolving localhost (localhost)... ::1, 127.0.0.1 Connecting to localhost (localhost)|::1|:80... connected. HTTP request sent, awaiting response... 403 Forbidden 2013-08-08 11:33:24 ERROR 403: Forbidden.
How we currently diagnose
tail -1 /var/log/httpd/error_log [Thu Aug 08 11:33] Permission denied: AH00132: file permissions deny server access: /var/www/html/index.html
Maybe SELinux?
kernel sends message to audit daemon.
auditd writes message to /var/log/audit/audit.log
ausearch -m avc -ts recent
----
time->Thu Aug 8 11:33:24 2013
type=PATH msg=audit(1375976004.652:1042): name="/var/www/html/index.html"
inode=3145858 dev=08:03 mode=0100644 ouid=0 ogid=0 rdev=00:00
obj=unconfined_u:object_r:user_home_t:s0
type=CWD msg=audit(1375976004.652:1042): cwd="/"
type=AVC msg=audit(1375976004.652:1042): avc: denied { read } pid=23276
comm="httpd" name="index.html" dev="sda3" ino=3145858
scontext=system_u:system_r:httpd_t:s0
tcontext=unconfined_u:object_r:user_home_t:s0 tclass=file
Setroubleshootd
writes message in /var/log/message
Aug 08 11:43:47 redsox setroubleshoot[24241]: SELinux is preventing /usr/sbin/httpd from read access on the file /var/www/html/index.html. For complete SELinux messages. run sealert -l fd6b9022-1ced-4065-905a-8f0e884f9915
writes analysys in /var/lib/setroubleshoot/setroubleshoot_database.xml
sealert
sealert -l fd6b9022-1ced-4065-905a-8f0e884f9915 SELinux is preventing /usr/sbin/httpd from read access on the file /var/www/html/index.html. ***** Plugin restorecon (92.2 confidence) suggests ************************ If you want to fix the label. /var/www/html/index.html default label should be httpd_sys_content_t. Then you can run restorecon. Do # /sbin/restorecon -v /var/www/html/index.html ...
System writes information all over the place
/var/log/httpd/error_log
/var/log/audit/audit.log
/var/log/messages
/var/lib/setroubleshoot/setroubleshoot_database.xml
SETroubleshoot integration with journald
type=AVC msg=audit(1375976004.652:1042): avc: denied { read } pid=23276
comm="httpd" name="index.html" dev="sda3" ino=3145858
scontext=system_u:system_r:httpd_t:s0
tcontext=unconfined_u:object_r:user_home_t:s0 tclass=file
Journald now allows privileged logging tools to reference other processes by PID
SETroubleshoot integration with journald
systemctl status httpd
# systemctl status -l httpd
httpd.service - The Apache HTTP Server
Loaded: loaded (/usr/lib/systemd/system/httpd.service; disabled)
Active: active (running) since Thu 2013-08-08 11:33:15 EDT; 45min ago
Main PID: 23272 (httpd)
Status: "Total requests: 4; Current requests/sec: 0; ..."
CGroup: /system.slice/httpd.service
...
Aug 08 11:33:15 redsox systemd[1]: Started The Apache HTTP Server.
Aug 08 11:33:23 redsox python[23287]: SELinux is preventing /usr/sbin/httpd
from read access on the file /var/www/html/index.html.
***** Plugin restorecon (
Secure Linux Containers
Labeled NFS
 https://access.redhat.com/site/videos/214723
https://access.redhat.com/site/videos/214723
IDM/FreeIPA supports SELinux Confined Users
At login sssd contacts FreeIPA for user@machine
Downloads /etc/selinux/targeted/logins
cat dwalsh sshd:staff_u:s0-s0:c0.c1023 *:guest_u:s0-s0:c0.c1023
sudo be configured by IPA with SELinux Config
dwalsh ALL=(ALL) TYPE=webadm_t ROLE=webadm_r ALL
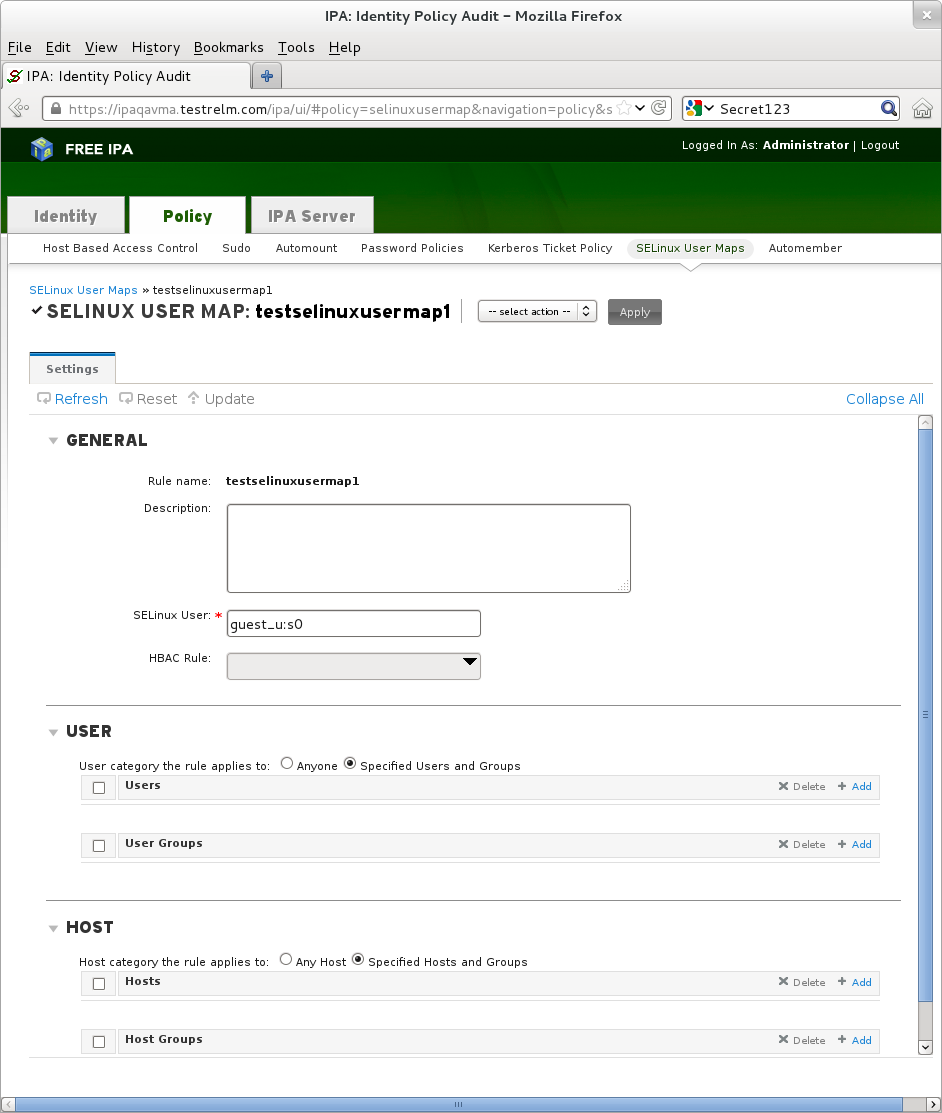
Confined Users
Active Directory
being worked on
Future
New coreutils
mv -Z
cp -Z
install -Z
mkdir -Z
Future
Friendly EPERM
questions?

Improving SELinux Usability
SELinux UXD usability tests in the GSS booth
Added > 700 Man pages for each confined domain
Adding GUI to be application focused
-
How does SELinux confine domain X?
- What booleans? What Types? What Network Ports?
- How can I modify them?